Selfish Mining - An Analysis
Ishaan Bhagat Princeton University
Independent Work Fall '24
Bitcoin operates on a decentralized ledger known as the blockchain, maintained by a network of miners who validate transactions and add new blocks to the chain. Miners are incentivized through block rewards—new bitcoins awarded for successfully adding a block. In this simplified scenario (assuming no transaction fees), miners compete to solve a computational puzzle, and the first to solve it broadcasts their block to the network.
Selfish mining is a strategy where miners aim to increase their share of Bitcoin block rewards by withholding newly mined blocks and releasing them strategically. Instead of immediately broadcasting a found block to the network, a selfish miner keeps it private, attempting to build a longer private chain. If the selfish miner can stay ahead of the public chain, they can release their private blocks to override the public chain, causing honest miners' efforts to be wasted on orphaned blocks. This manipulation is more effective when the miner controls a significant portion of the total mining power (denoted as α), as it increases the likelihood of maintaining a lead over the public chain and gaining disproportionate rewards.
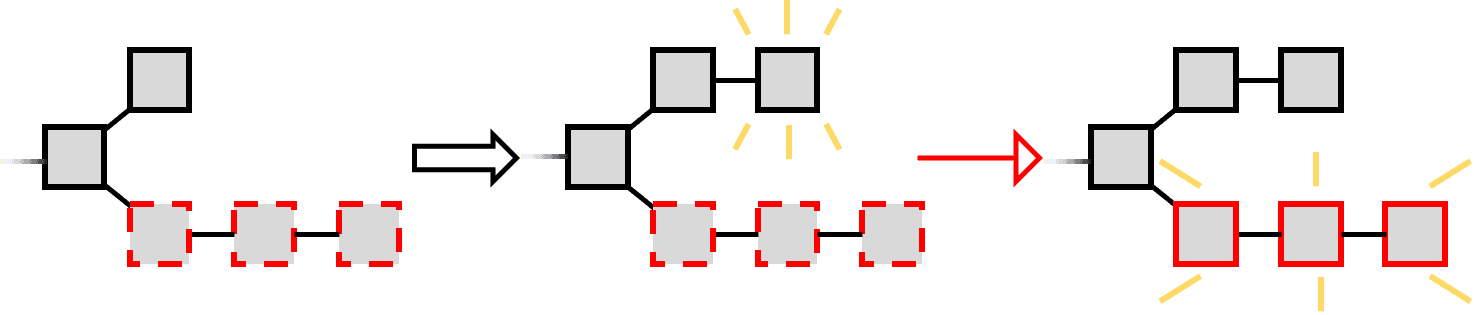
Selfish mining: at the bottom, we see a "hidden" selfish chain announced in order to invalidate the honest chain on top
While miners cannot forge transactions because digital signatures prevent unauthorized alterations, and they cannot retroactively change block contents due to the immutability enforced by hash pointers, nor can they permanently block a transaction because of the network's decentralization, they still have certain freedoms they can exploit. Miners are free to point to any block, not just the longest chain, and they can withhold or 'hide' any block they've found instead of broadcasting it immediately. They also have discretion over which valid transactions to include in the blocks they mine. By leveraging these abilities, miners can engage in strategies like selfish mining to gain an advantage without breaking Bitcoin's cryptographic security mechanisms.
To better understand the typical selfish mining strategy in action, let us set up a simplified Bitcoin game. We are making the key assumption here that you are already familiar with the fundamental Bitcoin basics found in the COS445 lecture notes.
Setup
Game:
Why set up the game like this?
The Longest Chain Protocol dictates that miners should always mine on the longest chain they know, broadcasting each block they create immediately. This protocol ensures that miners work together to maintain a single, continuous blockchain, preventing fragmentation. Let us set out this Longest Chain protocol formally:
Start / Reset
Consider the above example animation, showing an initial blockchain with all public blocks, and showing how a newly mined block would be inserted into the blockchain if the miner were to honestly follow the Longest Chain protocol.
Ideally, we would want this protocol to be a Nash equilibrium — meaning that no miner has an incentive to deviate from this strategy—because it would lead to stable, predictable growth of the blockchain, maximizing security and trust in the network. This would also minimize the eventual amount of orphan blocks, or legitimate blocks who've shown proof-of-work that do not eventually end up in the longest-chain.
However, this equilibrium fails if an adversarial miner holds more than 50% of the total mining power. Such a miner can ignore blocks from other miners entirely and create their own chain, which will eventually outpace all others. This gives the adversarial miner full control of the blockchain.
Unfortunately, even when an adversary has less than 50% of the mining power, the Longest Chain protocol is still not a Nash Equilibrium. A single miner can still yield higher profit over the Longest Chain protocol through selfish mining, where they withhold blocks to manipulate the network. By strategically releasing these blocks, the selfish miner can increase the chances of their blocks being accepted over those of honest miners, disrupting the longest-chain consensus and gaining an outsized share of rewards. Let's proceed to formally set out the seflish mining attack.
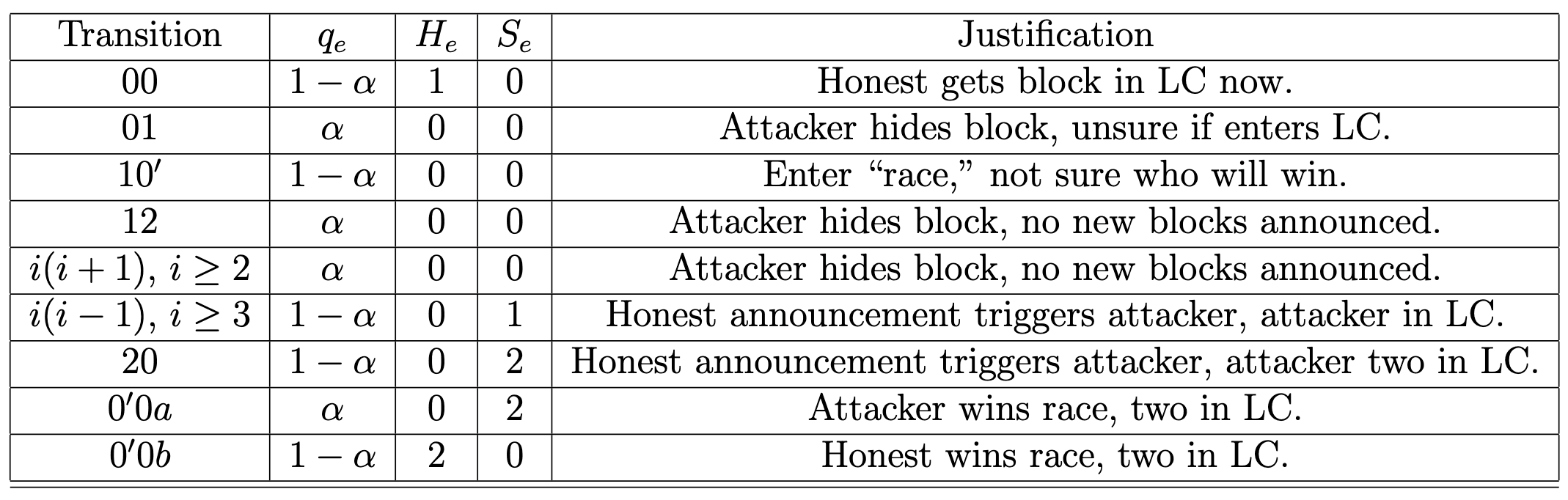
Counting scheme in tabular format, indexed through transitions with explanations

VIsual representation of Markov Chain, each state represents number of selfish hidden blocks
Selfish Mining - Final Understanding Quiz
Q1. In the selfish mining strategy, what is the purpose of hiding mined blocks? \\ \\ 1. To avoid detection by the network.\\ 2. To waste the honest miners' computational resources. \\ 3. To immediately extend the longest chain.\\ 4. To prevent tie-breaking among honest miners.